2021 Kubecon Takeaways: A Mixed Bag

Let’s get a few things out there right away.
First, Kubecon remains a shadow of its former self. In 2019 it was vibrant, even frothy. It was pretty sad this week in LA. The forecast was for 3,000 but we would be surprised if it was 2,000. My sense talking to others on the sponsor side was that online wasn’t any better.
Still, it was nice to talk to people 1:1 again. The conversations were few and far between, but as a result, they were not rushed. Still, I hope that the CNCF finds a way to get back to normalcy because this experience simply isn’t worth the investment.
Second, the CNCF is walking the walk with regard to diversity and inclusion. It is great to see on so many levels and the opportunities presented to speakers and leaders today will reshape the demographics for years to come as their talent shows through. Well done.
Third, from a technical perspective, Kubecon was a very different show from 2019 when we last saw each other in person. It comes through clearly in the themes from the show and underscores the speed with which Kubernetes has transformed enterprise technology. This can be seen in the talks and tracks but also in the companies that have the dollars to invest to be there in person. Here were the things that we took away this year. For previous posts check out 2020 and 2019.
Macro Theme – Operationalizing Kubernetes
On a macro basis, a big theme this year was around the operationalization of Kubernetes. This comes in various forms and flavors which we will outline below, but overall, the industry is thinking about Day 2 operations, not Day 1. The attendees are deeply versed in the concepts of containerization and orchestration. This is not an educational show, this is an advanced practitioners show. The traffic we got at MinIO was from existing users. Less than 1% of the questions had to do with “what is object storage” – everyone knows that Kubernetes favors object and as a result 70% of our traffic was familiar with MinIO – because they use it today in their work.
So what does operationalization look like?
- Observability – we will take a broad perspective on the term but ultimately there is a tremendous amount of interest in correlating each and every available data source. This is what separates mere monitoring from actionable insight. The current thinking goes well beyond the simple collection of logs, metrics and traces from individual applications and services within the cluster. Modern observability architectures find the relationships that facilitate an understanding of the complex events taking place deep within your clusters. Kubernetes is particularly challenging in this regard. It is complex, multi-layered and highly dynamic. It includes resources and services. It is a problem worth solving and has the appropriate amount of attention.
- Governance – the concept of governance for the container ecosystem has attracted a significant amount of attention in the last couple of years and speaks to the next level problem associated with the cloud-native way of doing things. Enterprises may still be rolling out 300 VMs every three months, but they are rolling out 3,000 containers every 3 hours. The difference is measured in orders of magnitude. This has real implications. The CNCF does a nice job of breaking down governance into its core dimensions. They talk about two things, policy scope, meaning where a specific rule should be applied, enforced, or verified and policy targets, relating to what should be enforced and verified. The subject matter is quite diverse and worthy of its own post but suffice to say there is material on security policies, access permissions, networking, applications and configuration. Again, a great example of the maturation of Kubernetes is the attention given to these areas.
- Security – security is ubiquitous these days, that is a given. The general foundations don’t change for Kubernetes, but the implementation path is more complex and with complexity comes risk. There are a number of elements here from Role Based Access Control (RBAC) to use process whitelisting and isolating Kubernetes nodes but the overall theme is that security needs to be part of the design, trust does not.
- Management – You know you are approaching a maturity plateau when cost management solutions proliferate the way they are at Kubecon. There must have been a dozen solutions on the floor dedicated only to the management of cost associated with container growth – particularly in the various public clouds. This is a good thing ultimately, as the cloud bill surprises are a thing and they are only good for the cloud provider – everyone else is a loser.
Beyond Operationalization, Multi and Edge
While the general theme of operationalization speaks to the maturation of the Kubernetes ecosystem – there are still areas that require work and innovation. Two that were front and center included multi-cloud and the edge.
Multi-Cloud
Multi-cloud is the next great push for the Kubernetes community.
AWS is seen, rightly or wrongly, as an entity to be wary of. There is a palpable sense in talking to people that optionality and freedom from AWS lock-in is a requirement, not a nice to have. Further, you get the sense, and this is anecdotal, that GCP and Azure are making headway in winning hearts and minds. I even heard a customer mention Oracle as something they were looking at. Granted it seems to be based on price more than performance, but that too is a sign of maturity. Either way, the multi-cloud genie is out of the bottle and the impact can be seen by enterprises seeking consistent storage, while they seek diversity in compute.
As we know, this presents distinct challenges. GCP, Azure, Oracle etc, don’t speak S3 fluently. Given the precision required for Kubernetes, this is very problematic. To have portable data in the Kubernetes context you need portable object storage and that is exactly what MinIO has created.
Needless to say, this challenge benefits MinIO disproportionately as the only true multi-cloud object store in existence (every public cloud, every K8s distro, private cloud, edge). It is what makes us so popular in the Kubernetes community.
We have written extensively on the subject here and here so we won’t recap. Looking back, we flagged the multi-cloud in our 2019 wrap but it now comes standard, courtesy of Kubernetes.
Edge
The edge is an interesting area for the Kubernetes community. Kubernetes was not designed for the edge, but has found its footing there. When you think about it for a moment, it makes sense. In the case of failure at the edge (a default part of any design), Kubernetes already knows how to react - which is the same way it does when dealing with a failed node - it reroutes the traffic.
There are some cool initiatives such as K3’s and microK8s that apply the same architecture but to smaller footprint. Edge storage is a ultimately a container game and containers need orchestration.
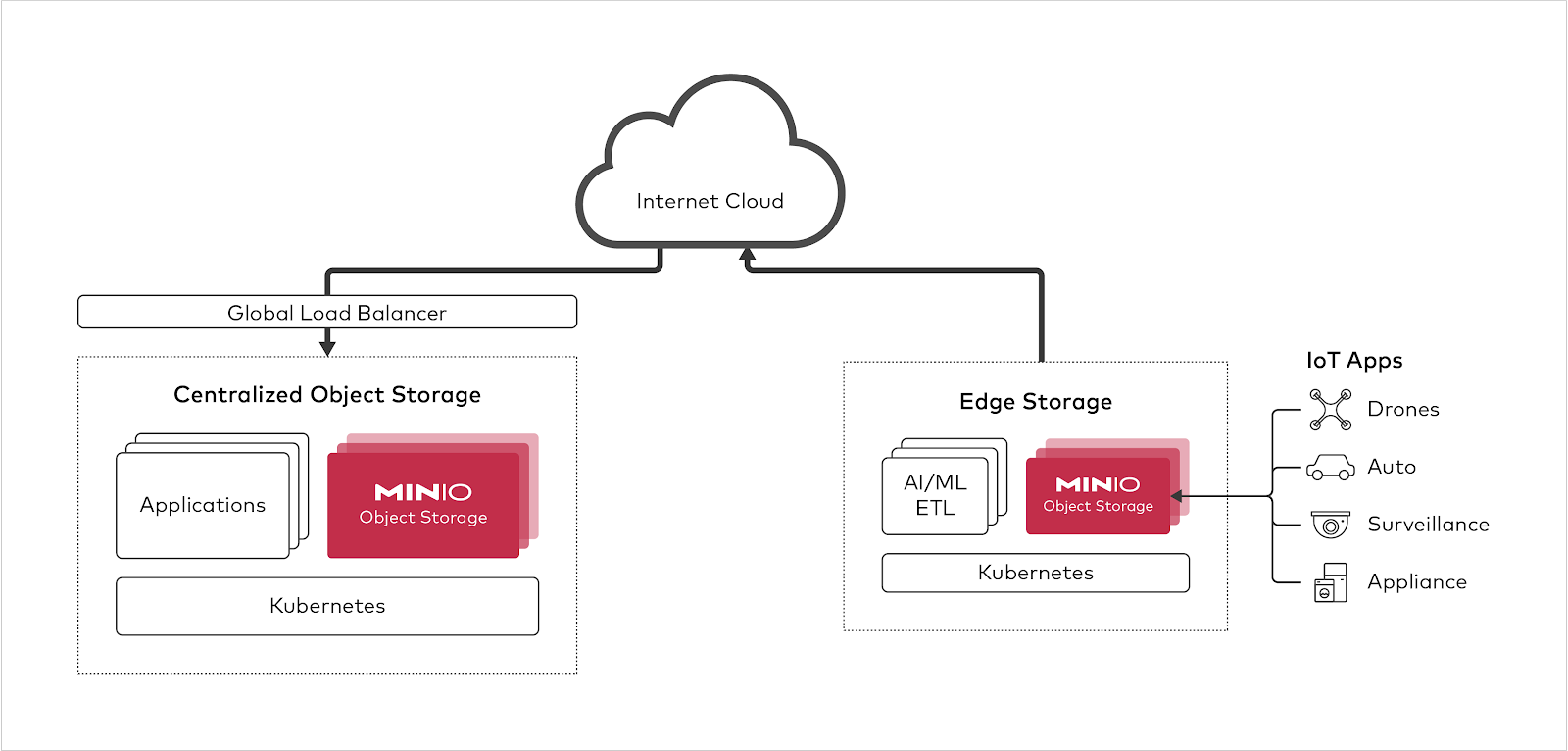
From a storage perspective the requirements are clear for Kubernetes at the edge:
- Software Defined to run on heterogenous HW
- Lightweight to run in constrained spaces
- Resilient in the face of minimal resources
- Performant to process data in situ, saving precious bandwidth dollars
- Secure - which means the ability to run fully encrypted from bleeding edge to edge to data center
The vendor community is still figuring out some of the other parts (see above) based on our conversations but those who are focused on the edge are successfully rolling their own today. We expect more “reference architectures” to begin to appear over the next few quarters.
Summary
While it was not a “great” Kubecon - it was an important one. It marked, for us at least, our first in-person show. It marked an important step forward on the diversity front and it marked some major maturity milestones for the technology. Let us know if you have any thoughts to the contrary. You can pipe in on our general Slack channel or drop us a note on hello@min.io.






