Frictionless Encryption
If you handle data of any kind, you have to worry about data security. This is true for multinational banks; it’s also true for small and medium-size businesses. Encryption should never be your only line of defense against malicious actors, but it is one of the most basic security best practices that every organization should consider essential.
However, not all encryption schemes provide the same level of protection. While every major storage provider offers some kind of encryption, the details vary enough for real-world security consequences. It’s easy to get caught up in analyzing encryption algorithms (more on that below), but high-performance encryption is at least as important: If encryption is turned off because of a real or perceived performance hit, it does not matter how well the encryption algorithm works.
If you care about security, you need to look deeper than just whether or not data is encrypted in transit and at rest. Here are some of the encryption-related details to consider as you compare storage options.
Transparency in how encryption is managed
Amazon Web Services (AWS) provides little details about how exactly encryption is handled in the Simple Storage Service (S3) object stores. They claim to use the AES 256 block cipher as the core primitive, but otherwise there’s no information about how this primitive is used to encrypt the data. This isn’t enough information to evaluate how secure the encryption scheme really is.
As an open-source project, transparency is core to how MinIO operates. Not only do we have extensive documentation about not just which encryption algorithm we use, but are in the process of publishing a provable chain — something to watch for in the coming weeks.
No performance hit
There’s a myth that encryption shouldn’t be enabled in high-performance use cases. Some types of encryption schemes are in fact a drag on performance, which makes users more likely to turn encryption off when speed is important. From a security perspective, this is a terrible idea: just because data is collected in a high-performance setting doesn’t mean it should not be protected. In addition, this data persists in the system, presenting a logistical nightmare as unencrypted data continues to accumulate.
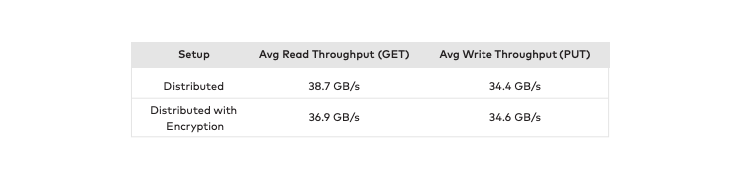
MinIO’s encryption scheme actually operates faster than other parts of the system, so there is no difference in performance when encryption is enabled. The evidence can be found in our NVMe and HDD benchmarks where we run them with encryption enabled and disabled.
We recommend all of our customers simply enable encryption all the time to ensure that all data is kept secure. Unlike with other encryption solutions, there is no downside to consistent encryption.
For some industries, encryption is non-optional. Banks, for example, simply had to take the performance hit because encryption is a requirement. With MinIO’s high performance encryption, even highly regulated industries can have performant, data-rich applications without compromising on security.
Secure channel ensures both confidentiality and integrity
In general, encryption schemes, like AES-CBC or AES-CTR, ensure confidentiality but don’t provide any data integrity protection. Authenticated Encryption with Associated Data (AEAD) schemes, like AES-GCM, do provide integrity in addition to confidentiality but only when processing the entire data as one continuous block atomically. They are not designed for processing data as a stream, which is how any S3-compatible storage solution operates.
At MinIO, we use an AEAD — either AES-256-GCM or ChaCha20-Poly1305 — as the foundation for a secure channel that ensures both confidentiality and integrity for streaming data. In particular, we rely on an analyzed and well-understood design.
MinIO is the only object storage solution that offers this level of protection, covering both data confidentiality while also protecting against data tampering.
Ensure integrity
With the type of encryption used by AWS or Ceph, it’s probably not possible for a malicious user to gain access to the data itself. However, a malicious user could change the data undetected.
For example, on your blog you might serve some content — e.g. photos of dogs — actually stored in an encrypted S3 bucket. Now, you may expect that even though those photos are public information — anyone visiting your blog can see them — nobody, even with direct access to storage disks, should be able to change the content to e.g. photos of cats. Unfortunately, if your data is encrypted with AES-CTR that it is trivial to change your beloved dogs for cats. Depending on the exact details, it is also possible to make the swap when the data is encrypted with AES-GCM.
MinIO’s encryption protocol ensures not only the confidentiality of your data, but also the integrity. If data has been altered in any way, you will be alerted. While data integrity is not often thought about as an encryption problem, it is a major part of the overall data security landscape.
Always on
Encryption isn’t something that can be enabled entirely by default. When a customer sets up MinIO or any other object storage solution, he or she needs to provide encryption keys. However, once this initial step is completed, MinIO’s encryption is always on. Because there is no performance hit, there’s no reason to disable it for individual use cases.
Security breaches are often caused by human error, not a technology failure. An ad-hoc approach to encryption, with encryption enabled in some use cases but disabled in others, requires more manual steps and more opportunities for error. MinIO’s encryption, on the other hand, is something customers can set and forget, dramatically reducing the likelihood that human error will leave sensitive data exposed.
Learn more
With MinIO, you don’t have to ‘just trust us’ that encryption is done correctly—we’re fully transparent about how it works. You can read more on GitHub or in our documentation. Further you can join the conversation on Slack, or reach out to us on hello@min.io






