Integrate MinIO with Keycloak OIDC

Keycloak is a Single-Sign On solution. Using Keycloak users authenticate with Keycloak rather than MinIO. Without Keycloak you would have to create a separate identity for each user - that would be cumbersome to manage in the long run. You would want a central identity solution to manage authentication and authorization for MinIO. In this blog post, we’ll show you how to set up MinIO to work with Keycloak. But broadly it should also give you an idea of how OIDC is configured with MinIO so you can use it with anything other than Keycloak, here we just use it as an example.
How to Set Up Keycloak
Here we are launching Keycloak as a docker container to get it quickly up and running for testing. But in production environments follow the Kubernetes deployment method to use with MinIO.
Let’s go ahead and install keycloak
Git clone the keycloak containers repo
Launch keycloak instance
Once that is launched, access keycloak at http://localhost:9080 using the below credentials
Follow the steps below to configure Keycloak to work with MinIO. These would be followed in the Keycloak UI.
Step 1:
Step 2:
Step 3:
Step 4:
Step 5:
Step 6:
Step 7:
Step 8:
Copy the following to MinIO ENV var MINIO_IDENTITY_OPENID_CLIENT_SECRET
Like so
Next let's configure this with MinIO
Configuring with MinIO
We’ll show you a couple of different ways to configure this with MinIO. First with a bare metal install and second with Kubernetes.
If you are launching it in bare metal or docker, you can `export` the following env vars
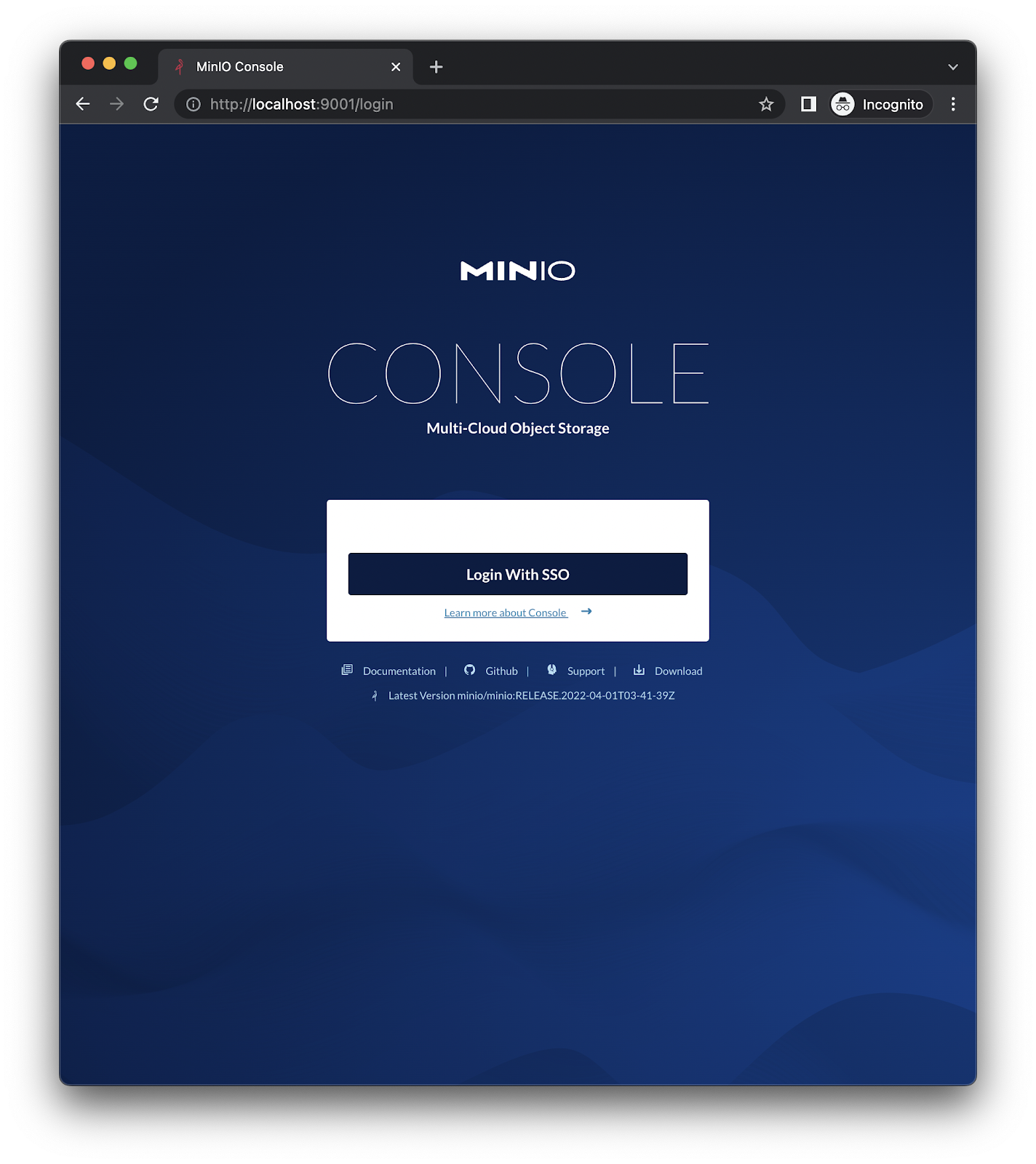
Then login with SSO at http://localhost:9001/login
If you are using Tenant Operator, its somewhat a similar process. Set the following env vars in tenant spec
- Note 1: MINIO_BROWSER_REDIRECT_URL is the console UI. It must be exposed publicly from the node port into the cluster to port forward to the public IP.
- Note 2: MINIO_IDENTITY_OPENID_CONFIG_URL is our keycloak exposed publicly, this also needs to be port forwarded and a public IP address set. The expectation is that SSO is configured the same way with a public way to connect to similar software, and can be auth0 as well.
Access tenant using SSO
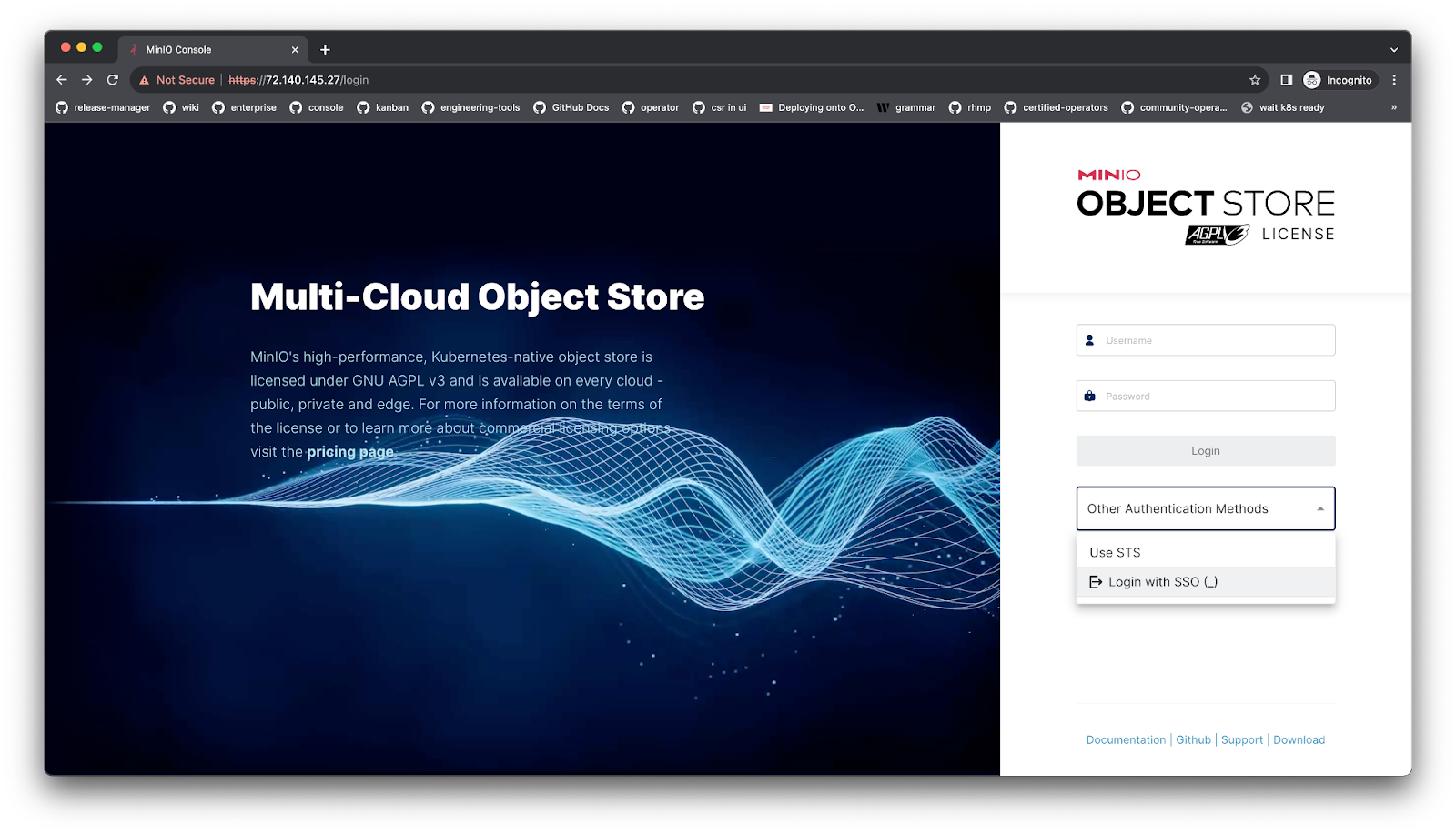
The rest of the process is the same whether its bare metal, docker or Kubernetes. Provide your MinIO login credentials.
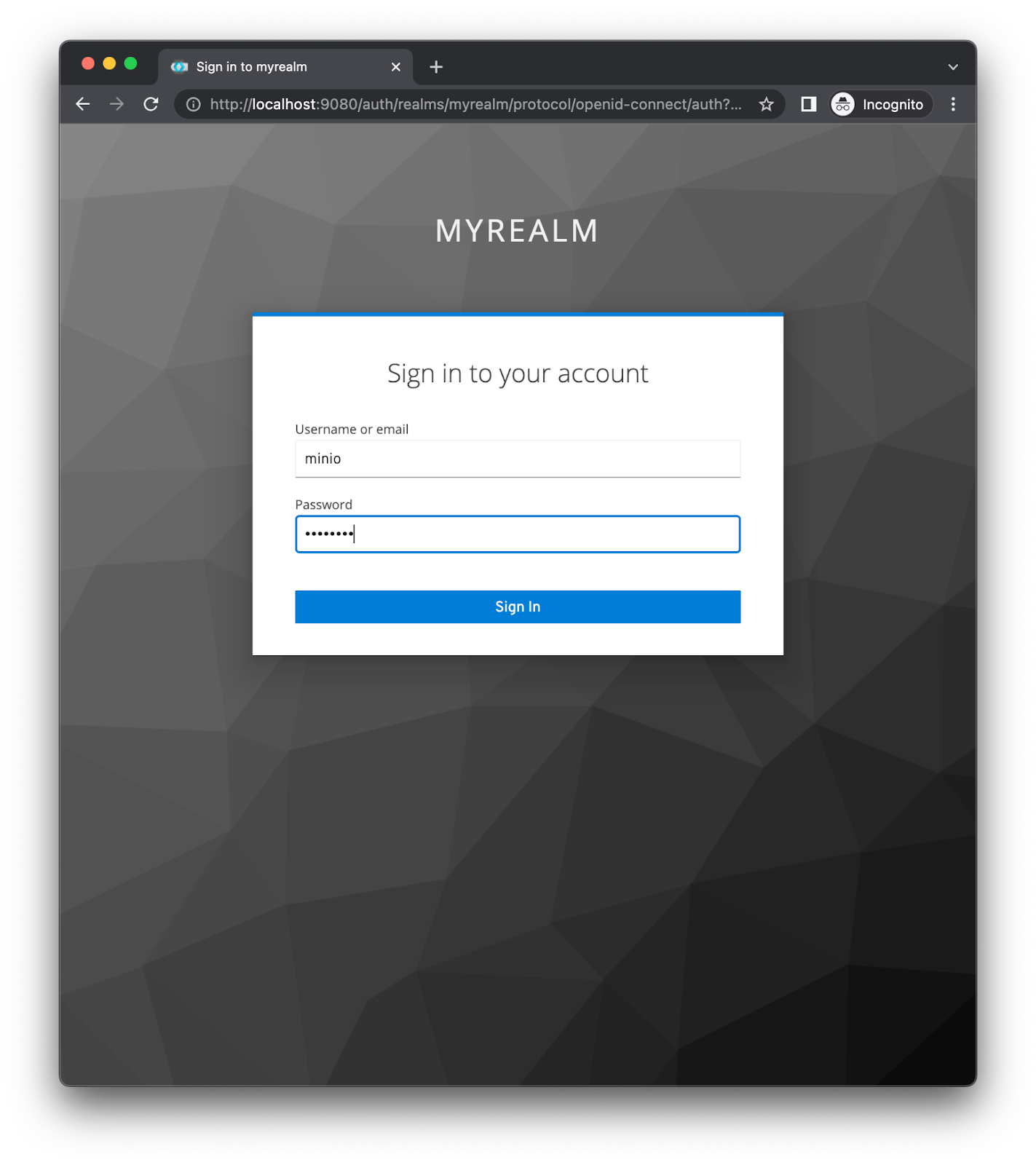
As expected you should see a UI like below
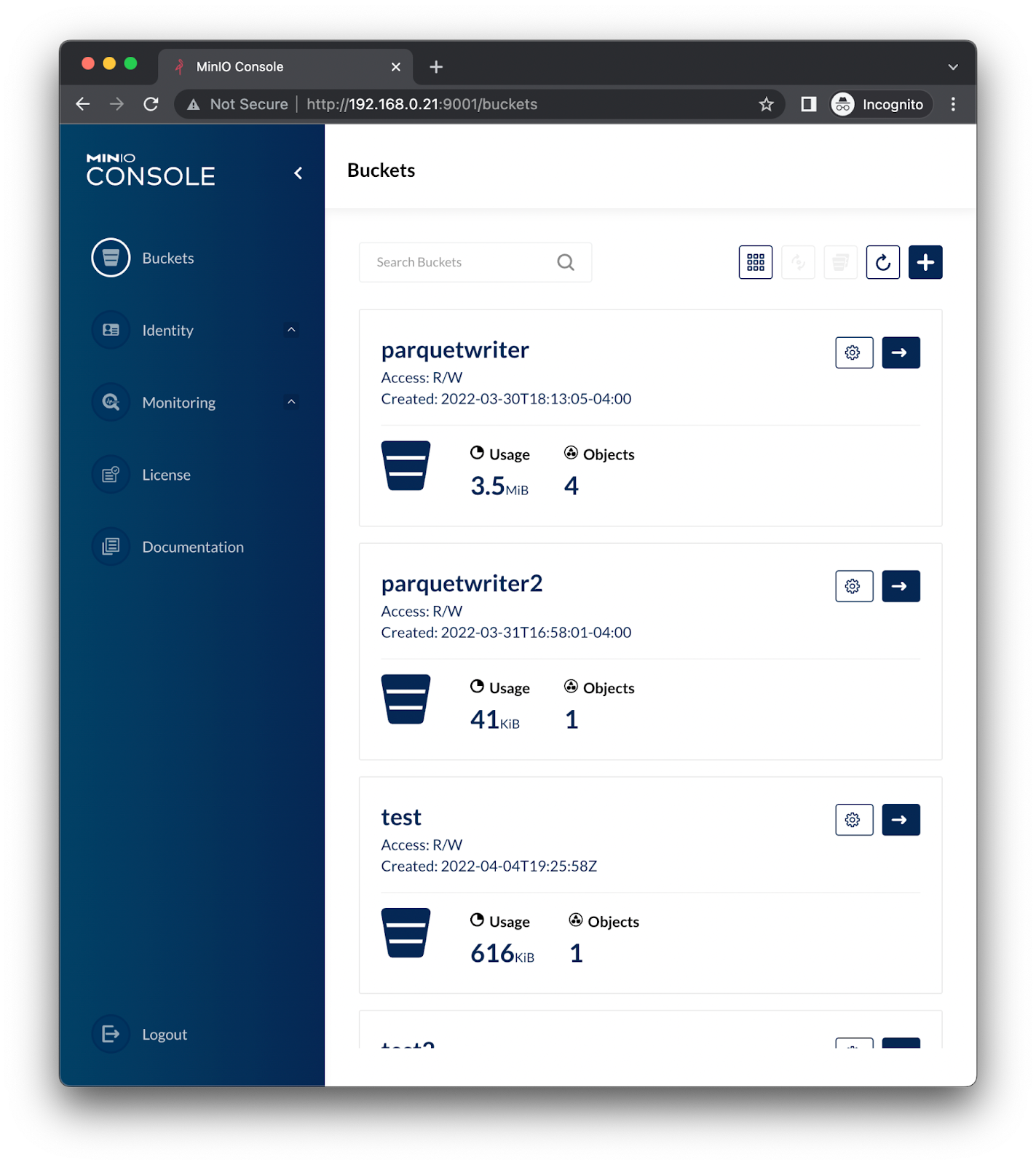
It's as simple as that.
Final Thoughts
As you can see, there is not much to do to get OIDC tools such as Keycloak to be integrated with MinIO. You just need to configure the OIDC tool to accept authentication requests from MinIO and set up MinIO to redirect to your OIDC tool. You can now use this real working example to configure your own OIDC.
If you have any questions regarding MinIO’s OICD integration or any SSO questions in general, be sure to reach out to us on Slack!






