The App Store of OpenShift: MinIO in OperatorHub

Running AI data storage infrastructure in the cloud is very expensive. Not only is it expensive to store the data, but everytime your applications consume the data from your AI data storage infrastructure you get charged ingress and egress fees. At one point when cloud was new and the scale of the data was small the costs were negligible. But with cloud costs rising industries have been looking to repatriate their data from the cloud without losing out on the cloud native benefits. That is the key here, repatriating out of the cloud without losing the ability to manage your infrastructure cloud natively.
That is where OpenShift OperatorHub comes in. One of the driving proponents of the cloud repatriation movement is OpenShift. OpenShift brings world-class cloud native ability to manage Kubernetes right on your own infrastructure from your own data center. Simply put, OperatorHub to OpenShift is what App Store is to Apple. With a web console interface, an Operator can be pulled from its off-cluster source, installed and subscribed on the cluster, and made ready for engineering teams to self-service manage the product across deployment environments.
Today we’ll show you how to install the MinIO operator using OperatorHub. In the process we’ll show you how to set up and test your local testing environment while using OpenShift with MinIO operator.
MinIO Operator via OperatorHub
Be sure to install crc on your Ubuntu machine. To learn more about CRC please refresh with this blog post.
MinIO Operator Console
Expose the operator open web page http://localhost:9090/login and get the token from the secret
oc login -u kubeadmin https://api.crc.testing:6443
oc port-forward svc/console 9090 -n openshift-operators
Apply these permissions to be able to create the namespace and get its quotas and this somehow will gain access to display the storage class in OpenShift
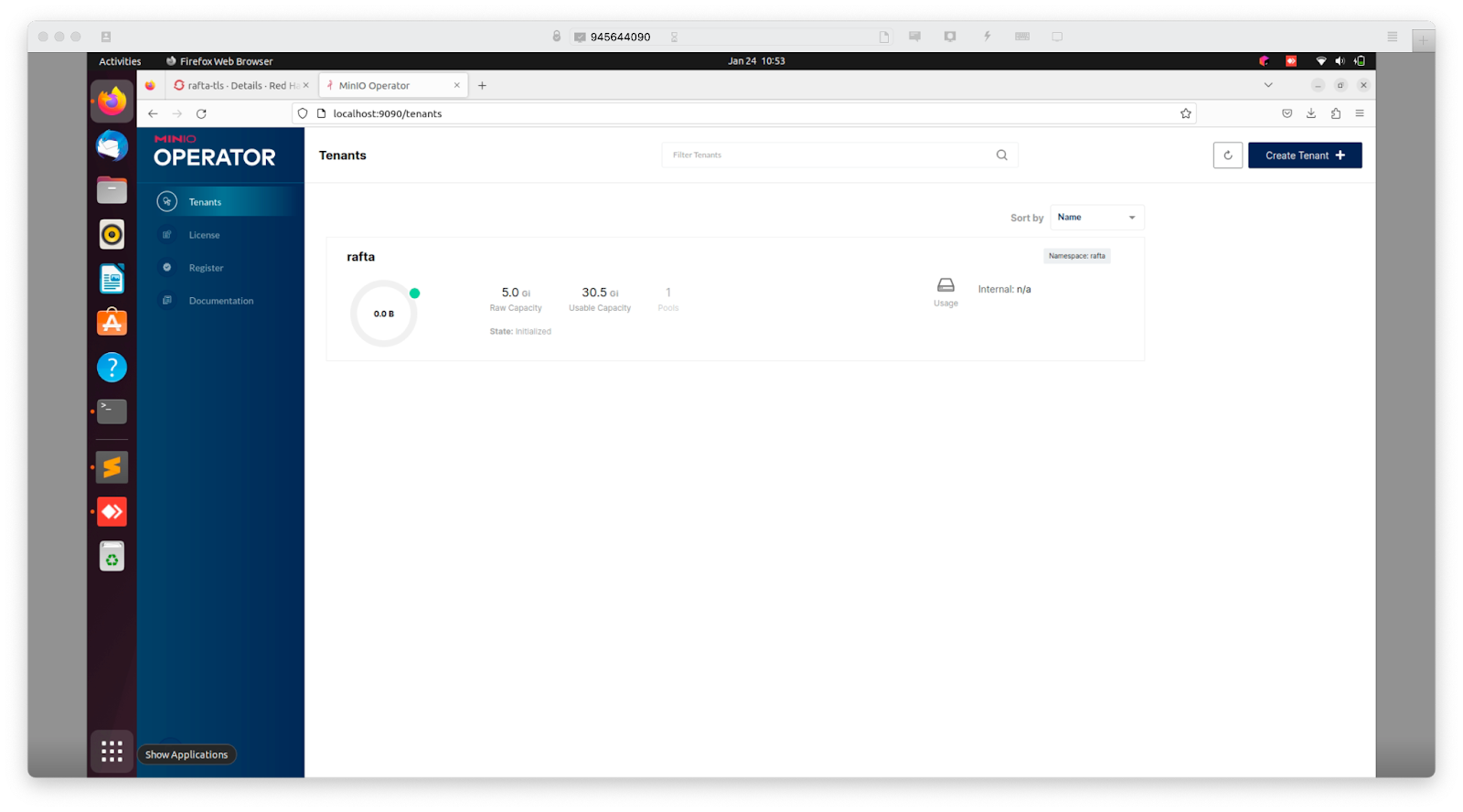
Create MinIO Tenant
Via the operator console create a tenant
Access Key: STSKAzp1TAsd9TGV
Secret Key: XzMOmH6erHeXzBM8dWAsf5LlOfSRKw7kThen see the issue after pod is created
ERROR Unable to initialize backend: parity validation returned an error: parity 4 should be less than or equal to 0 <- (4, 1), for pool(1st)To correct go to the tenant configuration http://localhost:9090/namespaces/rafta/tenants/rafta/configuration and change EC:4 by EC:0
Updating Cert
In order for TLS to work we have to update the certs used by the MinIO operator, let’s go ahead and do that.
First generate the certificate of the signer
Then, put together the above cert along with its signer in a file called ingress.pem.
Create a secret using the ingress.pem file above and the private.key from previous step
Patch it using kubectl, and wait for couple of minutes for the cert to be located at /var/run/secrets/kubernetes.io/serviceaccount/ca.crt.
Wait a few moments while things get ready after the change and Operator will work and be able to communicate
Operator App Store
OperatorHub is the de facto App Store of Operators for the OpenShift ecosystem. The operators that get listed on OperatorHub are thoroughly tested, vetted and supported by their respective authors. The authors can range from community operators to certified operators (such as MinIO) and also RedHat themselves. This gives your organization peace of mind knowing that the operators your developers are installed call be trusted with security and compliance. Because they have access to very critical pieces of infrastructure and you don’t want to just install some random operator from a GitHub repo which might degrade the performance of your system or in the worst case compromise it. So its paramount that your developers are given access to such Operator Marketplaces so they can build the infrastructure needed to power your application.
If you have any questions on the MinIO Operator or how to install it on an OpenShift cluster, be sure to reach out to us on Slack!






