Ransomware in 2022: Protect Your Backups
In 2022, every business must take precautions to protect against the serious threat of ransomware. In 2020 and 2021, we saw an increase in the number and severity of ransomware attacks, and 2022 promises to continue this fearsome trend. According to BlackFog, in 2021 there was a record total of 292 reported ransomware attacks. Of these, more than 80% involved data exfiltration with records and victim information found for sale on the Dark Web.
Ransomware attacks are constantly evolving, and this means new variants, vectors and methodology. REvil, which achieved notoriety after the Colonial Pipeline attack, accounted for 17.5% of attacks. Conti saw an increase of 228% over 2020 to account for 16.8% of all variants found in 2021. We also saw the virtual elimination of Ryuk, MazeNefilim and DoppelPaymer as they fell out of favor with attackers.
In October 2021, ENISA, the European Union Agency for Cybersecurity, released the most recent edition of the ENISA Threat Landscape report, which analyzed online crime between April 2020 and July 2021. The report serves as a wake-up call, as it declared that “this is the golden era of ransomware”, a period where the criminals are far more organized and effective than the law enforcement agencies charged with stopping them.
If you don’t want to be the next Kronos, or JBS, or Kaseya, then please read on.
Prevention is the Key
The ENISA report includes several tactics to decrease the chances of ransomware infection. Firstly, organizations must have the right threat intelligence at hand so that the “whole cybersecurity community [can] develop the techniques needed to best prevent and respond to this type of attacks.” Operating systems and software must be kept up to date with the latest security patches to prevent criminals from exploiting known vulnerabilities. Multi-factor authentication is considered a must-have to prevent account compromise. Organizations are encouraged to develop a mitigation strategy that includes secure backups, so in the event of a ransomware attack, systems can be restored without paying the ransom.
Let’s focus on backups and how the paradigm must evolve to prevent ransomware. It is likely that your organization established a backup strategy years ago, before the rise of ransomware, and it is focused on surviving failure or accidental deletion, not on surviving an attack. This is significant, because once a ransomware gang gets access to your network and storage, they will delete all backups so that you have no recourse but to pay them to unencrypt your data.
MinIO for Secure Backup
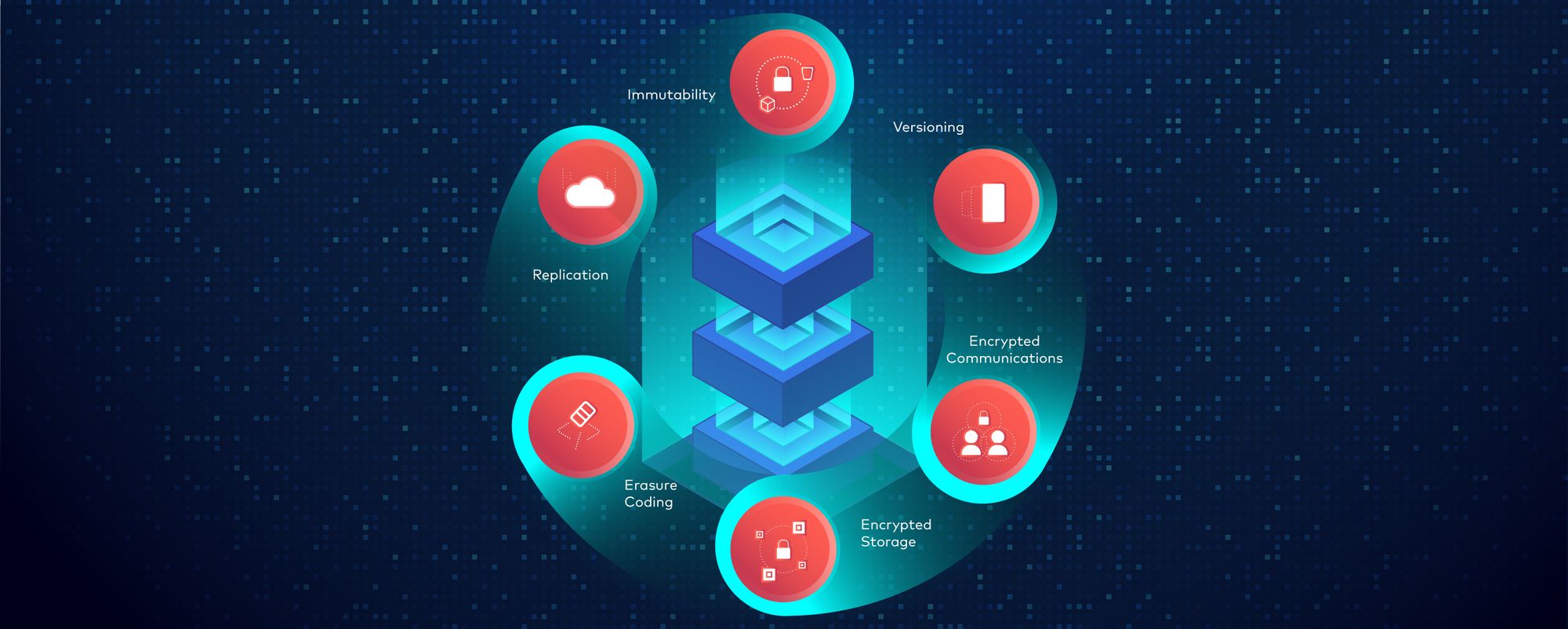
MinIO includes features to securely store backups and minimize the effects of ransomware. Key among these is the ability to prevent changes to backups, while providing secure, high-performance access to the data they hold.
Your backup strategy needs to take time windows for backup and recovery into account. Performance is of the utmost importance when building backup and recovery processes. It’s critical to choose a backup storage solution that provides the performance characteristics needed to meet your Recovery Time Objective. As the world’s fastest object storage, MinIO has the ability to read and write at speeds in excess of 349GB/s (read) and 177 GB/s (write), making for very efficient backup and recovery. All of the I/O from the backup software is committed synchronously to MinIO where the backup is encrypted and erasure coded for protection.
Objects written to MinIO are immutable, meaning that once they are written, they can not be tampered with. MinIO includes a full range of controls built around immutability, such as object locking, object retention, legal hold, governance mode and compliance mode. It’s worth noting that MinIO data immutability meets or exceeds Cohasset Certification Standards for electronic data storage. Ransomware can’t encrypt or delete data or backups that are saved to MinIO.
MinIO includes versioning capabilities that enable applications to retain multiple versions of an object within a bucket. MinIO version objects independently, consistent with AWS’s S3 structure/implementation. Every version of an object is assigned a unique ID, and applications can specify a version ID at any time to access the point-in-time snapshot of that object. Once a bucket is enabled for versioning, it can’t be turned off. Versioning protects data from ransomware because it preserves every version of every object - they can’t be deleted by bad actors.
Communications with MinIO using the API and the web interface are authenticated and encrypted. To protect data in transit, MinIO relies on TLS 1.2+ to encrypt data transmissions between applications and MinIO as well as MinIO’s own intracluster communications. To protect data stored on drives, MinIO supports granular object-level encryption using industry-standard algorithms such as AES-256-GCM, ChaCha20-Poly1305, and AES-CBC. Both in-transit and on-drive encryption is optimized at the CPU instruction level to provide the best possible performance. Encrypted data is protected from ransomware, malware and other malfeasance in-transit and at-rest.
Active-active replication between clouds means that objects are continuously being replicated between MinIO clusters. Replication is configured at the bucket level and includes the ability to replicate encrypted objects and their associated metadata, all object versions, object tags and object settings such as object locking. Within a MinIO cluster, data is written to drives and protected using erasure coding to provide resilience and data availability in the event that drives and/or nodes develop errors. If evidence of ransomware or other tampering is found in one cloud, applications can quickly be reconfigured to run against the MinIO instance to which data was replicated.
Resist Ransomware with Secure Backups
The same mechanisms that enable MinIO to store data in a tamper proof manner make MinIO a ransomware resistant home for your backups. Object storage has become the ubiquitous backup target for backup software as almost all of them can be configured to write to S3-compatible object storage such as MinIO. For example, MinIO was recently certified as a data protection target for Commvault. The software can use MinIO as a backup target or a backup source.
Commvault includes layered security controls that can be used in conjunction with the protections in MinIO listed above to prevent intentional bad actors such as ransomware from modifying or deleting backup data. Commvault uses end-to-end encryption and certificate authentication to protect against malicious data attacks. Only authorized Commvault processes are permitted to access backup data written to MinIO. In addition, Commvault leverages machine learning to detect file-based anomalies that may indicate a ransomware attack.
Here’s a sample of backup software that integrates with MinIO:
Getting Started
Strengthen your ransomware protections today by downloading MinIO. If you have any questions, ping us on hello@min.io or join the Slack community.






