Secure Multi-tenant Object Storage for Internal and External Apps

A common cloud-native architecture is to store data in object storage, such as MinIO, and make it available to a variety of applications, both internal and external. Data must be protected from inspection and tampering as it travels across networks, especially untrusted external networks. The standard for this is encryption using Transport Layer Security (TLS) v1.2+. MinIO Operator provides the ability to generate and allocate TLS certificates as part of the tenant deployment process. MinIO supports the use of multiple TLS certificates for each tenant, where each certificate corresponds to a specific domain name. MinIO uses Server Name Indication (SNI) to provide the right certificate for a given request.
Since Day One, MinIO has included encryption functionality to secure data at rest and in transit. When sensitive data over the wire, such as STS credentials, passwords or the objects themself, you can have peace of mind knowing they will be delivered to MinIO in a confidential and secure way.
In this post you will learn how to:
- Install MinIO Operator
- Deploy a MinIO tenant
- Add external TLS certificates to tenants
- Access MinIO tenants using different domains (SNI support)
Installing MinIO Operator
In your Kubernetes cluster install MinIO Operator via krew:
Alternatively, you can also install the operator manually:
Login to Operator
If you installed operator via krew, then run:
Copy the JWT (JSON Web Token), open a browser and go to http://localhost:9090
If you manually installed operator, then you need to expose the operator service using the kubectl port-foward command, and then manually extract the authentication token:
Copy the JWT to the login form and press Login.

Deploy a new MinIO tenant
Before we start, let’s take a moment to describe our overall solution. Suppose you have the following requirement:
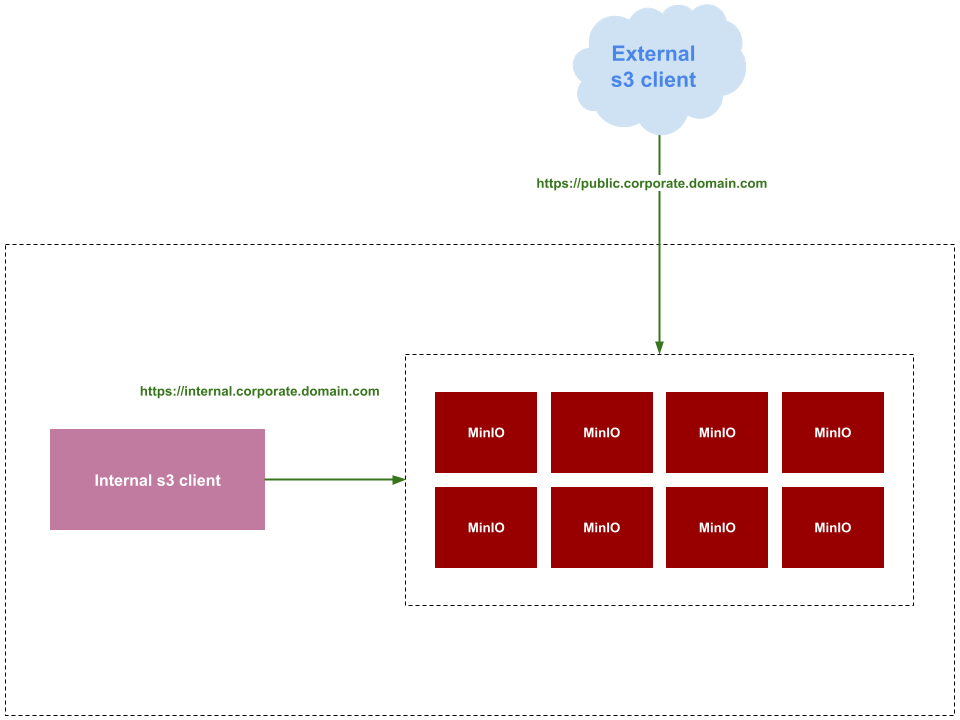
To accomplish this, you will need a MinIO tenant deployed inside the Kubernetes cluster that is accessible by both internal and external clients, and not only that, they will use different domains. Let’s do it.
From your browser, in the MinIO Operator, click the Create Tenant button. You will be presented with the following screen.
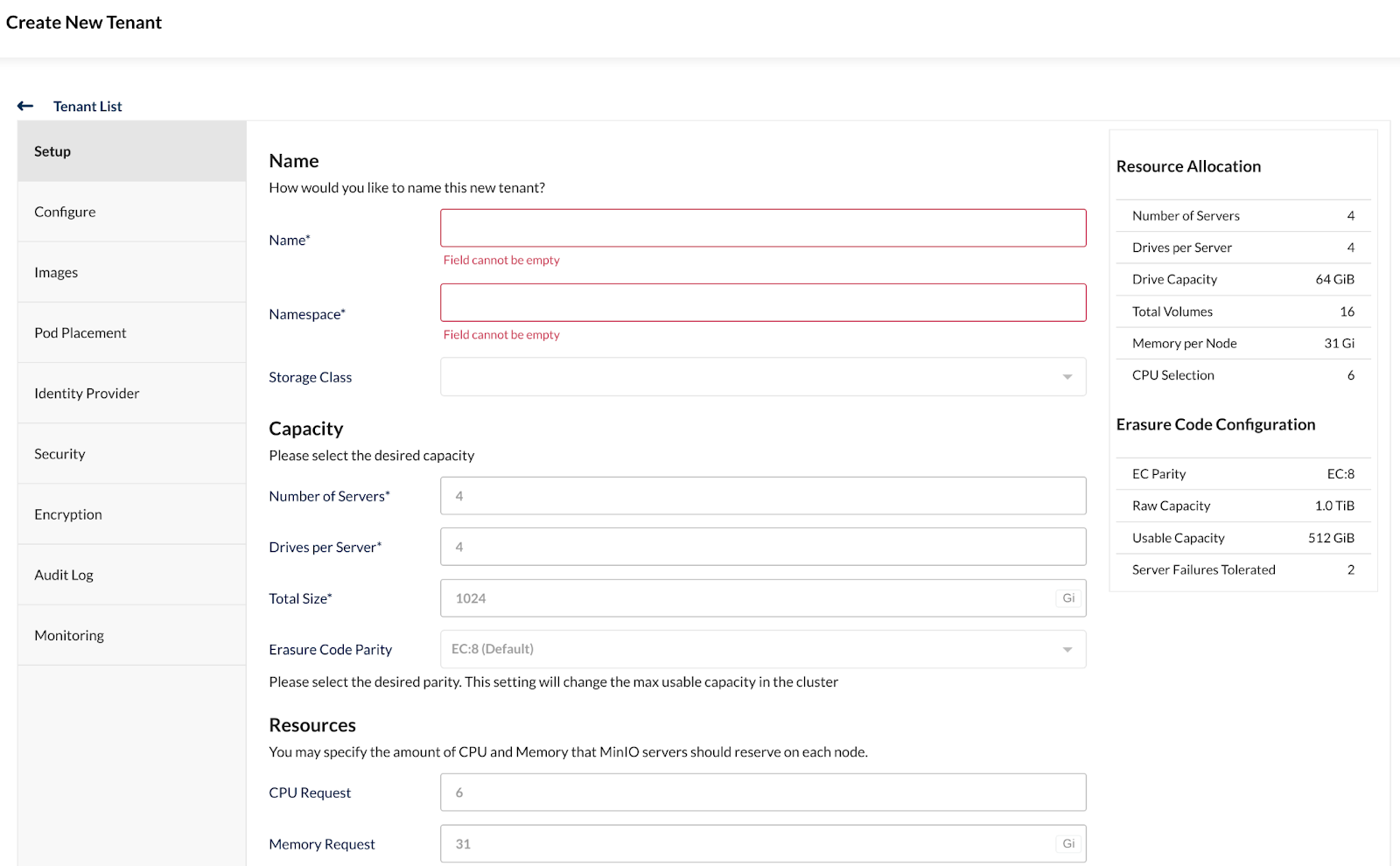
You can configure your tenant with details such as name, namespace, capacity, number of nodes, etc. You can explore the sub menus that contain additional options to tweak your tenant. Click on the Security menu.
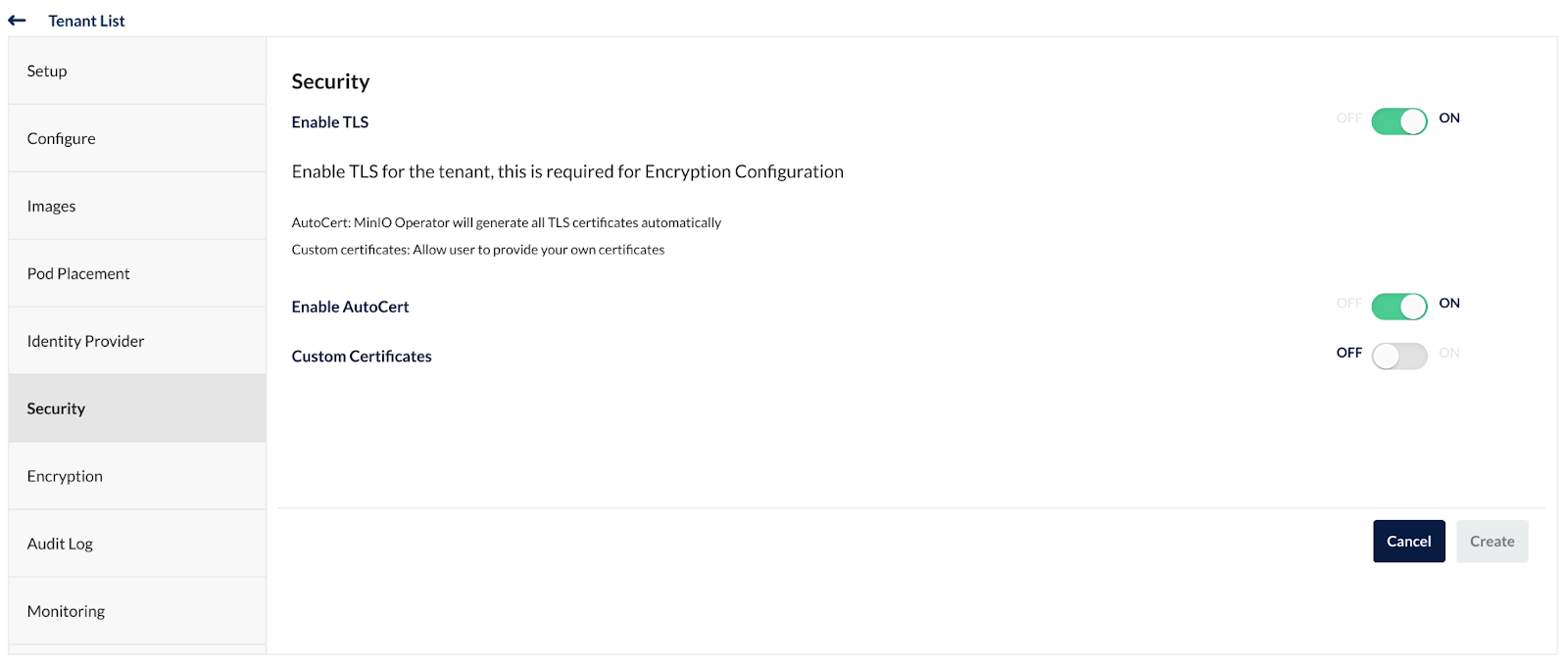
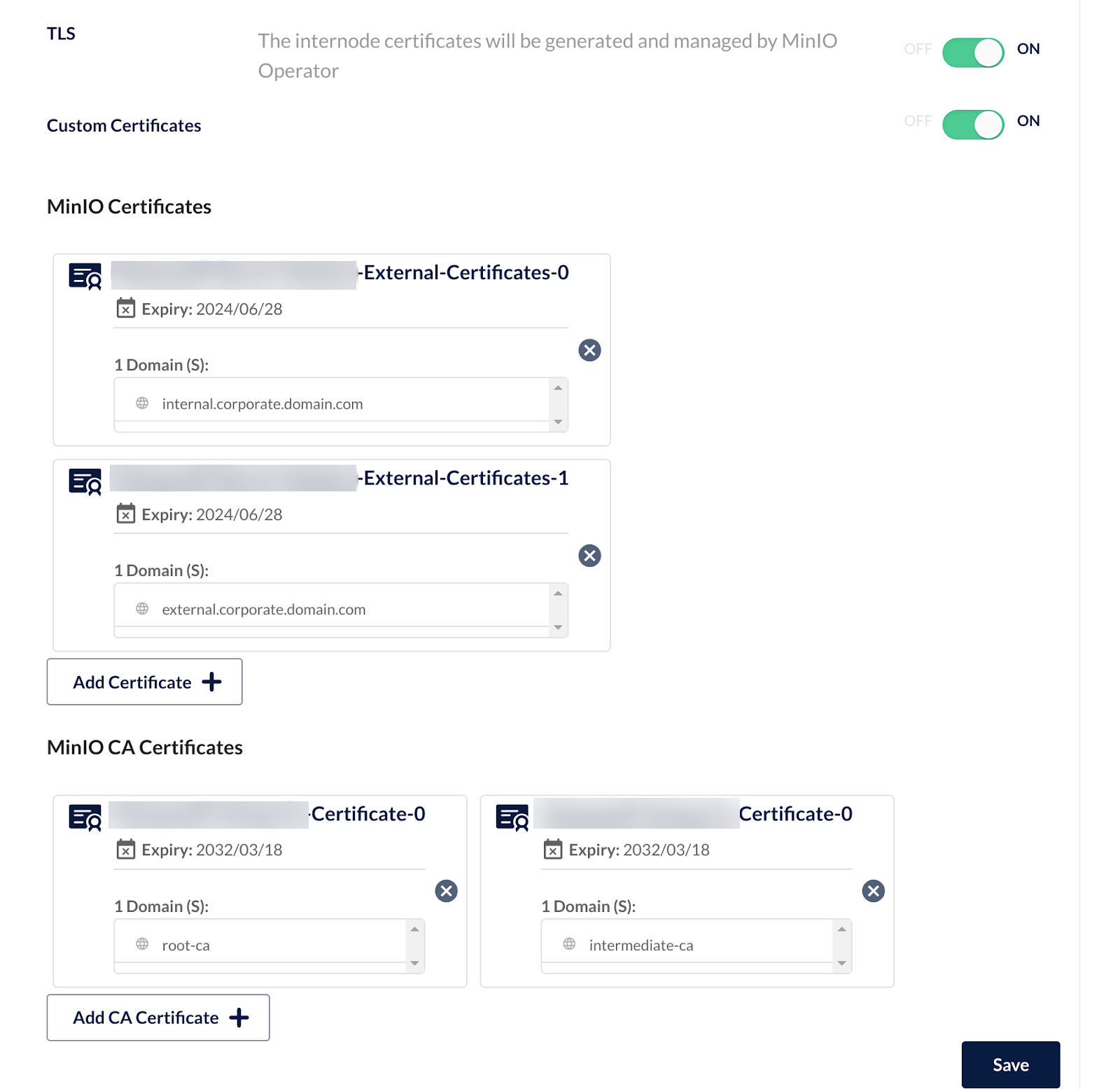
In the Security menu, you can see MinIO Operator will automatically generate certificates to secure internode communications, but what about your internal and external domain certificates?
Click on custom certificates and you will see additional options to upload your own certificates. These are usually a public.crt and private.key file.
You can upload as many certificate keypairs as you need - and thanks to SNI support MinIO will know the right certificate to return for each client.
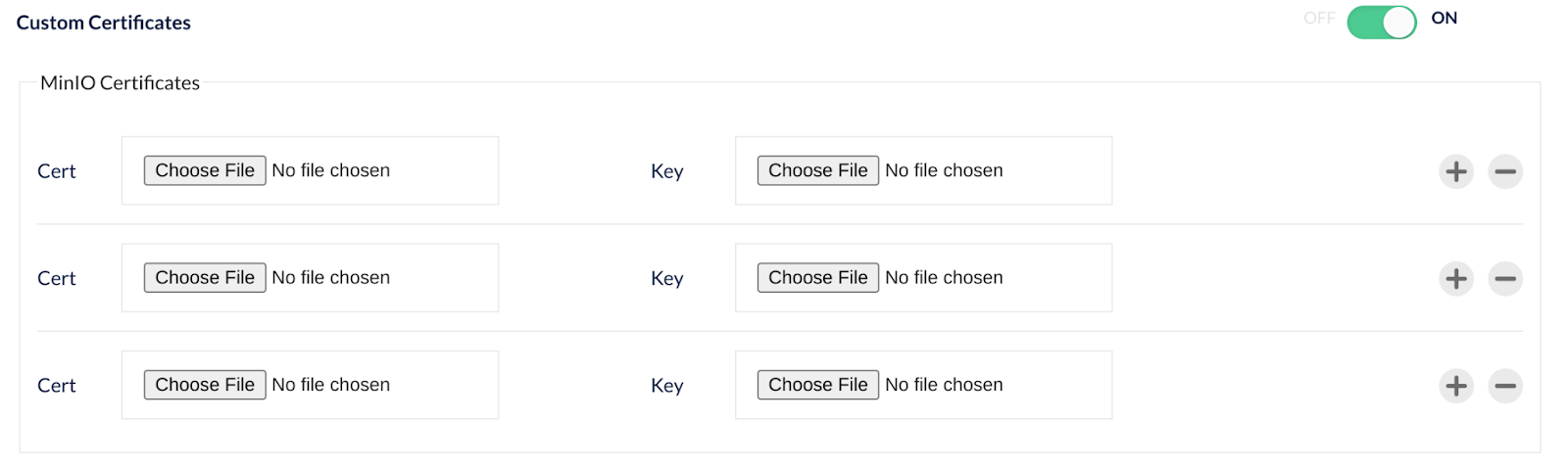
When you are ready click Create.
After a few minutes your tenant will be online. Return to the Security tab and you will see your custom certificates are configured. From this screen, you can add additional certificates and remove or rotate existing ones if needed.
Now you need to expose your Kubernetes service. Use your preferred method: NodePort, LoadBalancer or Ingress controller. For reference, we have a tutorial about using NGINX with MinIO.
Verify the TLS Certificates
Once the tenant is exposed to internal and external clients, it is very easy to verify that SNI is working properly using openssl:
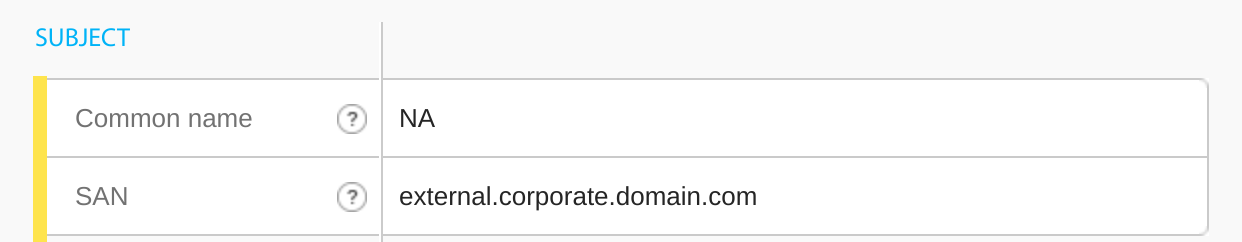
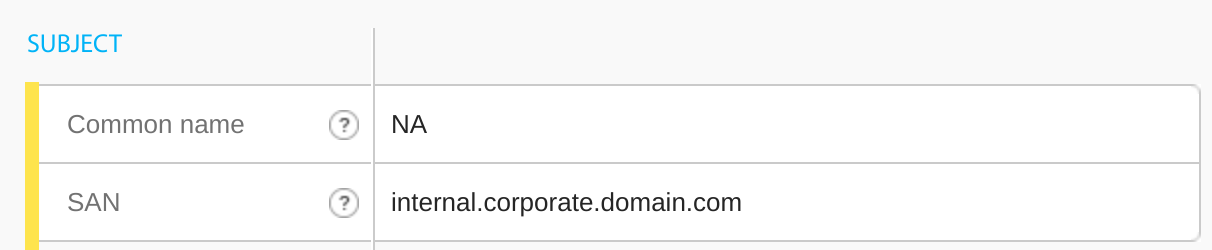
Copy the encoded certificates and go to https://www.sslchecker.com/certdecoder to confirm your domains are correct. You can decode a certificate with openssl using openssl x509 -text -in filename.
Important Notes
Configuring multiple certificates, for example internal and external, for MinIO tenants may appear cumbersome, but the effort is far outweighed by the benefit. When certificates expire, you will have to rotate two certificates instead of only one. However, from a security perspective it’s better to separate your internal and external domain certificates because the information on them is public and you’ve just seen how easy they are to decode!
TLS certificates are a good source of information for attackers when planning and conducting reconnaissance. The information they contain may divulge details of your internal infrastructure. Careful planning on your part is needed to find the right balance between security and functionality when designing your multi-tenant certificate strategy.
Conclusion
MinIO encrypts data when stored on disk and when in-transit. CPU instruction level optimizations enable encryption and decryption to take place with negligible performance overhead. MinIO customers leverage secure multi-tenant Kubernetes deployments to make S3 compatible object storage available to cloud-native applications for programs such as data lake analytics and streaming AI/ML. Multi-tenancy increases hardware efficiency and decreases cost. MinIO secures each tenant separately, and encrypts data saved on drives and transmitted across the network. MinIO is fully compatible with S3 encryption semantics so you know your application will function seamlessly and securely. MinIO includes support for other key management services such as Hashicorp Vault and Gemalto KeySecure.
If you have any questions, ping us on hello@min.io or join the Slack community.






